Agent-Based vs. Agentless IT Asset Discovery
In IT asset discovery, the choice between agent-based and agentless methods depends on your organization's needs. Here's a quick breakdown:
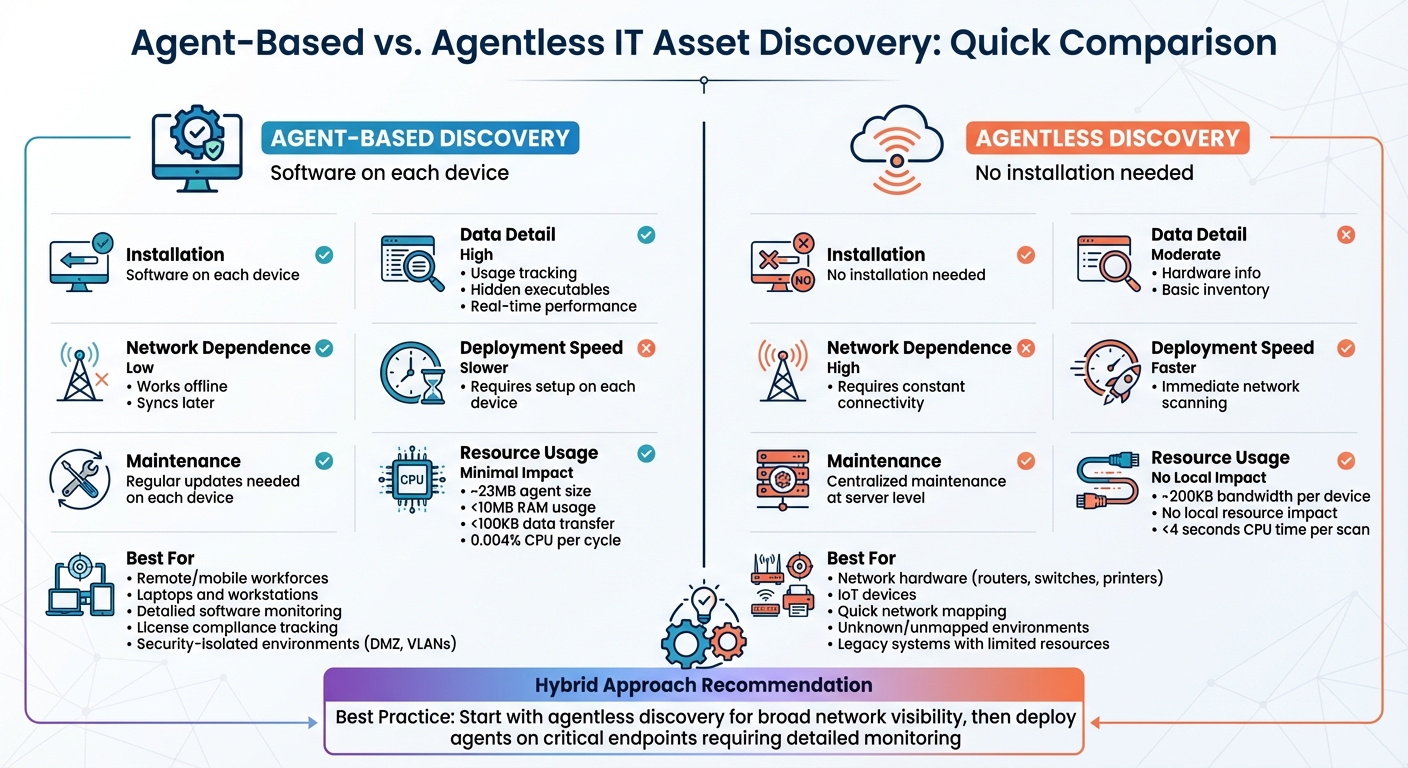
- Agent-Based Discovery: Involves installing lightweight software (agents) on devices to collect detailed data like hardware specs, software usage, and performance metrics. It works offline, syncs data later, and is great for remote workforces or environments with restricted network access. However, it requires installation, updates, and administrative effort.
- Agentless Discovery: Scans devices remotely using network protocols (e.g., SNMP, WMI, SSH). It’s faster to deploy, doesn’t require software installation, and is ideal for network hardware like routers, switches, and printers. But it needs constant network connectivity and provides less detailed data compared to agents.
Quick Comparison:
| Factor | Agent-Based Discovery | Agentless Discovery |
|---|---|---|
| Installation | Software on each device | No installation needed |
| Data Detail | High (e.g., usage tracking) | Moderate (e.g., hardware info) |
| Network Dependence | Low (works offline) | High (requires connectivity) |
| Deployment Speed | Slower (requires setup) | Faster |
| Maintenance | Regular updates needed | Centralized maintenance |
| Use Cases | Remote devices, detailed insights | Network hardware, quick scans |
A hybrid approach often works best: start with agentless discovery for broad visibility, then deploy agents where deeper monitoring is needed. This ensures a complete and efficient view of your IT environment.
Agent-Based vs Agentless IT Asset Discovery Comparison
Agentless vs. Agent-Based Asset Discovery - Infraon
sbb-itb-c68f633
What is Agent-Based IT Asset Discovery?
Agent-based discovery involves installing a lightweight software application directly onto devices like servers, laptops, desktops, and virtual machines. This software, known as an agent, collects detailed information about the device, including hardware specifications, installed software, usage patterns, and performance metrics like CPU and RAM usage.
Agents send this data to a central system at intervals you can configure - ranging from every 5 minutes to every 8–12 hours. For instance, the InvGate agent is only about 23MB and uses less than 10MB of RAM while running. It transmits compressed data packages under 100KB per transfer, ensuring minimal resource consumption. This method delivers precise and flexible insights into IT assets.
How Agent-Based Discovery Works
Unlike agentless discovery, which scans devices remotely, agent-based discovery provides much more detailed information by running directly on the target device. The process starts with deploying agents, which can be done manually, through remote scripts (like SSH or RPC), or via automated tools such as Group Policy Objects. Once installed, the agent creates a secure connection with the central server and begins monitoring the device.
"It gathers and stores data, transmitting hours, days, or even months of information in bulk when reconnected."
Agents also store data locally when offline, sending it in bulk once they reconnect to the network. This ensures that remote devices are continuously monitored. The process is efficient - agents typically consume only 0.004% of a device's CPU per discovery cycle and use about 200KB of network bandwidth per PC.
Benefits of Agent-Based Discovery
This approach has several advantages. Because agents operate directly on the target system, they can access system APIs to uncover hidden executables and monitor software usage in ways that remote scanning cannot. This makes agent-based discovery a powerful tool for IT asset management.
Another major benefit is network independence. Agents only require outbound communication to the central server, making them ideal for environments where inbound traffic is restricted, such as security-isolated VLANs. They are compatible with a wide range of operating systems, including Windows, macOS, Linux distributions (like Ubuntu, Debian, RHEL, and CentOS), and Android.
Challenges of Agent-Based Discovery
However, there are some drawbacks to consider. Deploying agents requires administrative privileges, which can be tricky - especially when you need an inventory of devices to install the agents, but the agents themselves are needed to create that inventory. Many organizations resolve this by starting with an agentless scan to identify endpoints before deploying agents for ongoing management.
Keeping agents updated is another challenge. Regular updates are necessary to ensure they remain functional and accurate, especially in environments with strict regulations, such as government agencies, where extensive security and privacy audits may be required before deployment. While modern agents are designed to be lightweight, administrators should monitor their impact on older systems or devices with limited resources to avoid performance issues.
What is Agentless IT Asset Discovery?
Agentless discovery plays a crucial role in IT asset management, offering a different approach compared to agent-based methods. Instead of installing software on individual devices, it scans predefined IP ranges to remotely gather data from network devices. A central engine handles the scanning, using configured credentials to access and collect configuration details from devices on the network.
This method relies on existing management protocols and APIs. For instance, it uses WMI or WinRM for Windows systems, SSH for Linux and Unix devices, and SNMP (versions 1, 2, or 3) for network hardware like routers, switches, and printers. Some tools also incorporate CIM for managing devices across different platforms.
"Agentless discovery reaches out to each server, attempts to 'log on' and or query the server using industry standard and/or manufacturer-specific protocols."
- Rick Johnston, Device42
Agentless discovery combines active scanning - directly contacting devices - and passive methods, such as analyzing network traffic with DPI or Netflow, to identify a variety of devices, including IoT sensors and specialized equipment like medical devices. It’s a zero-footprint approach, meaning it inventories devices through remote shares without requiring software installation.
How Agentless Discovery Works
The process starts by configuring a central discovery engine with IP ranges and administrative credentials (using protocols like WMI, SSH, or SNMP). This engine then polls the devices at scheduled intervals, collecting information like hardware specifications, software inventories, and performance metrics. It uses minimal resources - about 200 KB of bandwidth per device and very little CPU power.
However, without valid administrative credentials, the engine can only detect a device’s presence, limiting the depth of the data collected.
Benefits of Agentless Discovery
Agentless discovery offers several advantages, particularly in terms of deployment speed. Since there’s no need to install software on individual devices, it avoids the lengthy processes of change management approvals and security reviews often required for agent-based methods. Once the discovery engine is set up, it can immediately begin scanning the network.
"One of the main benefits of going the agentless route is that there are less political hurdles to leap in order to get the system deployed, since no local installation is required on the devices."
- Tracey Schaus, Flexera
This method is especially effective for network devices - like printers, routers, and IoT devices - that cannot host software. Passive techniques further enhance its capabilities by analyzing network traffic to identify device details. Additionally, maintenance is streamlined, as updates are managed centrally on the discovery server rather than on each endpoint.
Challenges of Agentless Discovery
Despite its advantages, agentless discovery has its limitations. For one, it depends heavily on network connectivity. Devices that are offline or remote, such as those used by mobile or remote workers, may not be detected.
Another drawback is the level of detail it provides. While it can inventory devices and gather performance metrics, it often cannot detect hidden software or track real-time application usage. This can hinder tasks like software license management or compliance audits. In fact, nearly 90% of AI usage in enterprise environments goes undetected without more robust tracking methods.
Network performance can also be impacted. Regular polling across the network generates more bandwidth usage compared to agent-based methods, which process data locally before sending it. In large-scale environments, deep scans may need to be scheduled during off-peak hours to avoid disrupting network operations. Additionally, local firewalls can block agentless discovery unless specific ports (e.g., RPC or WMI) are opened, whereas agents typically bypass these restrictions by "calling home".
Agent-Based vs. Agentless: Key Differences
When it comes to IT asset discovery, understanding the key differences between agent-based and agentless methods can help you make more informed decisions.
At its core, the distinction lies in how and where the discovery process happens. Agent-based discovery relies on software installed on each device. This software communicates with a central server using a pull-based, agent-initiated approach. On the other hand, agentless discovery takes a push-based, centralized route, where a central server scans the network to gather data directly from devices without installing software on them.
This difference introduces unique challenges. Rick Johnston from Device42 highlights a key hurdle for agent-based discovery:
"To track your inventory, you must first install agents; but if you do not already have your inventory tracked, from where is an administrator supposed to produce the complete list of machines that need agents installations...?"
Agentless discovery sidesteps this issue by scanning IP ranges to find devices, which makes it ideal for identifying unknown systems. However, it does require constant network connectivity, unlike agent-based discovery, which can operate offline and sync data later when the connection is restored.
Resource usage is another area where these methods diverge. Agent-based solutions are designed to be lightweight, using minimal local resources and transmitting small, compressed data packets. In contrast, agentless discovery generates significantly more network traffic - roughly 200 KB per device - because it relies on protocols like WMI or SNMP, which don’t allow for data compression.
Here’s a quick comparison of their differences:
Comparison Table: Deployment, Resource Usage, and Network Dependence
| Factor | Agent-Based Discovery | Agentless Discovery |
|---|---|---|
| Installation | Requires software on every target device | No software installed on targets |
| Deployment Method | Manual, remote (SSH/RPC), or mass deployment | Centralized network/IP range scanning |
| Target Resource Impact | Consumes local CPU and RAM | Minimal to no impact on target resources |
| Network Bandwidth | Low; data is often compressed and sent periodically | High; requires constant polling over the network |
| Network Dependence | Low; can collect data offline and sync later | High; requires active network connectivity |
| Maintenance | High; requires updates for each node | Low; centralized maintenance at the server |
| Data Granularity | High; detailed insights into local processes | Moderate; limited by SNMP/WMI protocols |
Pros and Cons of Each Method
When deciding between agent-based and agentless discovery, it's essential to weigh their strengths and challenges. Each approach offers distinct benefits and drawbacks that can influence your IT operations.
Agent-based discovery provides highly detailed insights, such as process monitoring, software usage, and even hidden executables. Since agents store data locally, they’re particularly effective for devices like laptops used by remote workers. These agents can collect data offline and sync it back to the network once connectivity is restored. On the flip side, deploying agents requires significant effort, including installation, patching, and updates for every endpoint.
Agentless discovery is quicker to implement since it doesn’t involve installing software on individual devices. Maintenance happens centrally at the server level, making it a good fit for network hardware like printers, routers, and switches that can’t host agents. However, this method relies heavily on network availability - poor connectivity can lead to incomplete data collection. Additionally, the level of detail is often limited by the capabilities of protocols like SNMP and WMI.
Pros and Cons Table
| Method | Pros | Cons |
|---|---|---|
| Agent-Based | • Provides detailed, real-time monitoring • Functions offline and syncs when reconnected • Consumes minimal network bandwidth (100KB–1MB per scan) |
• Requires ongoing maintenance (patching, troubleshooting) • Uses local CPU and RAM resources • High deployment effort |
| Agentless | • No installation needed on endpoints • Doesn’t impact device performance • Quick to deploy and scales easily |
• Consumes significant network bandwidth • Requires consistent network connectivity • Provides less detailed data compared to agents |
Security is another critical factor to consider. Agent-based discovery can introduce vulnerabilities if the agent software itself isn’t secure, requiring regular updates to address potential risks. On the other hand, agentless discovery involves storing administrative credentials on the central server and opening inbound ports, which could be exploited if the server is compromised.
"Caveat emptor - which roughly translates to buyer beware! Don't take any vendor simply at their word when it comes to such an important... purchase."
- Rick Johnston, Device42
When to Use Agent-Based IT Asset Discovery
Agent-based IT asset discovery shines in situations where device mobility or network restrictions demand ongoing, localized data collection. It’s particularly effective for tracking assets that move frequently or operate in environments with strict security measures.
For mobile assets like laptops, tablets, and smartphones - especially those used by employees traveling or working remotely - agent-based discovery ensures reliable tracking. These devices often disconnect from the corporate network or connect via VPN, making traditional network-based methods less effective.
In high-security setups, agent-based discovery is a practical choice. Devices in sensitive areas like de-militarized zones (DMZs) or isolated VLANs typically block inbound traffic for security reasons. Since agents use outbound communication to "call home", they bypass these restrictions without requiring changes to firewall configurations.
This approach is also ideal when detailed performance data is essential. Agents provide deep insights into system metrics, enabling tasks like license tracking, detecting unauthorized software, and monitoring real-time performance.
"An agent-based solution is often the best answer... for roaming users, and disconnected or inactive machines."
Agents are particularly effective in environments with unstable networks. They transmit small, encrypted data packets (often under 100KB) rather than relying on continuous network polling, making them well-suited for distributed networks with limited bandwidth.
Best Use Cases for Agent-Based Discovery
- Remote and Mobile Workforces: Agents are perfect for devices operating outside the corporate network. They continuously monitor hardware, software installations, and compliance, ensuring visibility even for offsite assets.
- Linux Environments: For patch management and discovery tasks requiring local software installation, agents are often essential. Certain operating system functions can only be accessed through locally installed agents.
- Shadow IT Detection: While agentless scans detect devices on the network, agents installed on corporate-owned machines can uncover hidden executables and unauthorized software that might otherwise go unnoticed.
- Real-Time Endpoint Control: For tasks like application monitoring, access tracking, or automated power management, agents offer unmatched capabilities. They can enforce policies, execute scheduled tasks like shutdowns, and monitor active processes directly at the device level.
For organizations with diverse asset types, a hybrid approach can be highly effective. Use agentless discovery for network devices like printers and switches, while deploying agents on endpoints that require deeper monitoring or often operate outside the network. This strategy balances broad visibility with detailed control over critical assets.
Next, we'll examine scenarios where an agentless approach might be a better fit.
When to Use Agentless IT Asset Discovery
Agentless discovery offers a fast and efficient way to gain visibility across large or unfamiliar networks. It's especially useful for devices that can't support agent installations or when minimizing maintenance is a priority.
This method proves invaluable during mergers and acquisitions. Often, the acquired company’s IT asset records are incomplete, making it impractical to install agents on potentially thousands of devices. Instead, agentless discovery can scan the entire network quickly and reconcile assets. As Sarah Coke, Senior Project Manager at Certero, explains:
"If you have a discovery tool that you can rely on to find 100% of your IT estate, you will initially need agentless technology".
Certain network infrastructure assets, like printers, routers, switches, and IoT devices, are inherently unsuitable for agent installations. According to Motadata:
"Agent-less is the only way for scanning SNMP assets like a printer, router, switches, etc.".
With projections indicating an average of 9.27 connected devices per person globally by 2025, the ability to discover non-computing hardware is becoming increasingly crucial. This capability also eases the workload on IT teams by automating asset identification.
For organizations with limited IT staff, agentless discovery offers another major advantage - there's no need to install, patch, or troubleshoot software on individual devices. Everything operates centrally. For example, one agentless solution uses less than 4 seconds of CPU time and about 200 kilobytes of network bandwidth per PC during a scan. Tracey Schaus from Flexera highlights another benefit:
"One of the main benefits of going the agentless route is that there are less political hurdles to leap in order to get the system deployed, since no local installation is required on the devices".
Best Use Cases for Agentless Discovery
Agentless discovery excels in scenarios where the network environment is unknown or unmapped. When there's no accurate inventory - or none at all - this approach scans defined IP ranges to uncover active assets. Rick Johnston from Device42 explains the challenge of agent-based discovery in such cases:
"To track your inventory, you must first install agents; but if you do not already have your inventory tracked, from where is an administrator supposed to produce the complete list of machines that need agents installations?".
Legacy systems and older hardware also benefit from agentless scanning. These devices often lack the resources to handle the overhead of running agents, so avoiding local installations helps preserve their limited CPU and RAM.
For detecting Shadow IT, agentless methods can identify unauthorized devices and IoT equipment that pose security risks. Scheduling scans during off-peak hours reduces the impact on network performance while helping pinpoint assets that may require closer monitoring.
In high-security environments, like data centers, policies often restrict third-party software installations on critical systems. Agentless discovery circumvents these restrictions by using protocols like SNMP, SSH, WMI, and WinRM to query devices remotely. However, it does require administrative credentials and only works for devices currently connected to the network.
Many organizations use agentless discovery as the first step in a hybrid strategy. It provides a complete overview of the IT estate, allowing teams to decide where to deploy more intensive agent-based monitoring for high-priority assets. This approach balances the strengths and limitations of both methods, ensuring comprehensive and efficient asset management.
Next, we’ll explore how to choose between these two approaches based on your organization’s specific needs.
How to Choose the Right Approach
Factors to Consider
When deciding between agent-based and agentless discovery, several practical factors come into play. Your choice will likely depend on the type of assets you're managing, the level of detail you need, your team's capacity, and your organization's security policies.
Agentless discovery works best for network infrastructure assets like printers, routers, switches, and IoT devices that can't host software. On the other hand, agent-based discovery excels with workstations where detailed performance and usage metrics are crucial. For remote employees or mobile workforces frequently disconnected from the network, agent-based methods are ideal. These agents collect data locally and sync it when a connection becomes available, while agentless discovery requires constant network access to function effectively.
If you're monitoring software license usage or ensuring compliance, agent-based discovery provides the granular data you need. In contrast, agentless discovery offers a basic inventory overview - good for identifying what's out there but not for understanding how it's being used.
Team capacity can also influence your decision. Agentless discovery involves a one-time network setup with minimal ongoing maintenance. Agent-based discovery, however, requires installing and maintaining agents on each device, which can be challenging for smaller IT teams. Though modern agents are lightweight (for example, InvGate's agent is approximately 23MB and uses less than 10MB of RAM), managing them at scale still demands effort.
Security policies might steer you one way or the other. As Tracey Schaus from Flexera points out, agentless discovery avoids the "bureaucratic red tape" often associated with installing third-party software on company devices. However, Rick Johnston highlights that agent-based discovery can be more secure in isolated VLANs where inbound scanning traffic isn't allowed. If your organization doesn't already have an asset list, agentless discovery offers a quick way to map your environment before deciding where agents might be beneficial.
Using Both Methods Together
Both approaches have distinct strengths, and combining them can provide the most comprehensive asset visibility. A hybrid strategy allows you to capitalize on the benefits of each. InvGate sums it up well:
"The true power of IT Asset Management lies in combining both approaches. By leveraging agent-based monitoring for granular details and agentless discovery for broader coverage, you'll have a comprehensive view of your IT ecosystem."
Start with agentless discovery to create a baseline map of your network, including shadow IT and unidentified devices. This is especially useful when your IT environment is largely unmapped.
After establishing this broad overview, deploy agents to critical workstations and laptops where detailed software usage tracking or license optimization is necessary. Use agentless methods for network infrastructure and legacy systems with limited resources, while reserving agents for assets needing deeper insights. This approach works well in data centers with strict change-control policies that favor solutions requiring no local software installation.
Tools like AdminRemix's AssetRemix can streamline IT asset management workflows, helping you organize and track assets identified through both methods. When selecting a discovery tool, ensure the vendor supports both approaches equally rather than prioritizing one over the other.
Conclusion
Key Takeaways
Deciding between agent-based and agentless discovery comes down to aligning each method's advantages with your organization's specific needs. Agent-based discovery provides detailed insights into software usage and real-time performance, making it crucial for monitoring license compliance and managing remote workers who often operate outside your network. With a lightweight footprint, agent-based discovery typically uses less than 10MB of RAM and sends encrypted data packages under 100KB. On the other hand, agentless discovery shines in quickly mapping your entire network, including devices like printers, routers, and IoT hardware that can't support software agents. Agentless scans, on average, use about 200KB per scan.
These differences highlight how each method serves a distinct purpose. Ignacio Graglia from InvGate emphasizes this balance:
"There is no one option better than the other. Actually, a combination leads to better results."
A hybrid approach leverages the strengths of both methods. Start with agentless scans to uncover all devices on your network, including shadow IT and unauthorized hardware. Then, deploy agents to critical assets like laptops and workstations for detailed software tracking and usage analytics. This dual strategy addresses blind spots while delivering deeper insights into your IT environment.
Ultimately, your choice should reflect the unique demands of your IT landscape. Consider factors like the types of devices in your network, the nature of your workforce (remote or on-site), your security protocols, and your team's capacity for ongoing maintenance. Tools such as AdminRemix's AssetRemix can help you manage assets discovered through both methods, streamlining workflows and improving efficiency.
Complete visibility is the cornerstone of effective IT asset management. Whether you opt for agent-based, agentless, or a combination of both, the right discovery method ensures you have a clear view of your IT environment. That clarity empowers you to secure and optimize your assets with confidence.
FAQs
Which devices should use agents vs. agentless scans?
Devices that frequently move within a corporate network or require detailed, ongoing monitoring are ideal candidates for agent-based scans. These scans offer in-depth insights into device activity and performance. On the other hand, devices such as printers, routers, and switches - commonly reliant on SNMP for network connectivity - are better suited for agentless scans, which work well for static, less complex devices.
What credentials and ports are needed for agentless discovery?
Agentless discovery usually needs outbound TCP port 443 access to certain cloud or management domains. The specific credentials required will vary based on the tool or service in use. Be sure to check the documentation for your platform to verify the necessary permissions and configurations.
How do I safely implement a hybrid discovery approach?
To effectively and securely use a hybrid discovery approach, blend agent-based and agentless methods to maximize their advantages. Agents are ideal for real-time monitoring of constantly changing assets, while agentless discovery works best for network devices or cloud systems where installing agents isn't feasible.
When deploying agents, prioritize security by using encryption and strict access controls. Roll out the implementation gradually, starting with critical assets, to ensure both security and smooth operations.